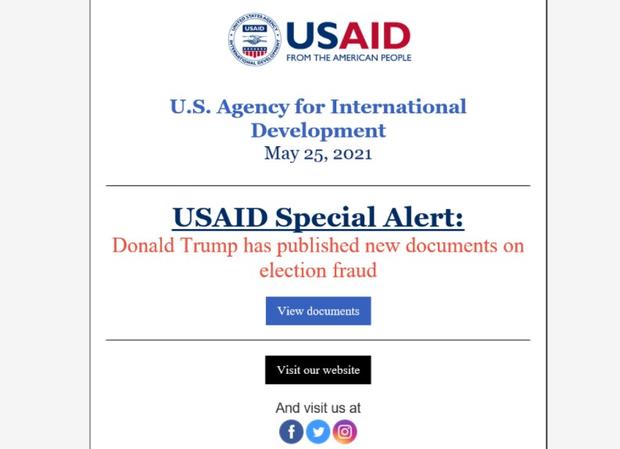
Boston — The state-backed Russian cyber spies behind the SolarWinds hacking campaign launched a targeted spear-phishing assault on U.S. and foreign government agencies and think tanks this week using an email marketing account of the U.S. Agency for International Development (USAID), Microsoft said.
The effort targeted about 3,000 email accounts at more than 150 different organizations, at least a quarter of them involved in international development, humanitarian and human rights work, Microsoft Vice President Tom Burt said in a blog post late Thursday.
The New York Times notes that many of the targeted groups are the types that have been critical of Russian President Vladimir Putin.
Burt’s post didn’t say which attempts may have led to successful intrusions.
A spokesperson for the U.S. Cybersecurity and Infrastructure Security Agency (CISA) told CBS News, “We are aware of the potential compromise at USAID through an email marketing platform and are working with the FBI and USAID to better understand the extent of the compromise and assist potential victims.”
The cybersecurity firm Volexity, which also tracked the campaign but has less visibility into email systems than Microsoft , said in a post that relatively low detection rates of the phishing emails suggest the attacker was “likely having some success in breaching targets.”
Burt said the campaign appeared to be a continuation of multiple efforts by the Russian hackers to “target government agencies involved in foreign policy as part of intelligence gathering efforts.” He said the targets spanned at least 24 countries.
The hackers gained access to USAID’s account at Constant Contact, an email marketing service, Microsoft said. The authentic-looking phishing emails dated May 25 purport to contain new information on 2020 election fraud claims and include a link to malware that enables hackers to “achieve persistent access to compromised machines.”
Microsoft said in a separate blog post that the campaign is ongoing and evolved out of several waves of spear-phishing campaigns it first detected in January that escalated to the mass-mailings of this week.
While the SolarWinds campaign, which infiltrated dozens of private sector companies and think tanks as well as at least nine U.S. government agencies, was supremely stealthy and went on for most of 2020 before being detected in December by the cybersecurity firm FireEye, this campaign is what cybersecurity researchers call “noisy,” meaning easy to detect.
Microsoft noted the two mass distribution methods used: the SolarWinds hack exploited the supply chain of a trusted technology provider’s software updates; this campaign piggybacked on a mass email provider.
With both methods, the company said, the hackers undermine trust in the technology ecosystem.
In the blog post, Burt said, “Nation-state cyberattacks aren’t slowing. We need clear rules governing nation-state conduct in cyberspace and clear expectations of the consequences for violation of those rules.”